CrowdStrike 2QFY26 Earnings: The Flex Flywheel Ignites
Why the Market Missed the Most Transformative Quarter in CrowdStrike’s Platform Evolution
TLDR:
Consumption Economics Takes Over: Falcon Flex customers are re-upping 50% larger contracts in just five months—proof that CrowdStrike’s platform model drives non-linear expansion and behavioral lock-in.
SIEM Disruption Accelerates: The ONUM acquisition eliminates migration bottlenecks, turning Falcon-native data into a structural cost and performance advantage over legacy players like Splunk.
AI as a Reinforcing Loop: Charlotte’s AI capabilities grow stronger with every customer, creating an economic moat rooted in proprietary MDR telemetry—translating into operational efficiency and future margin expansion.
"CrowdStrike Holdings swung to a second-quarter loss and guided for lower third-quarter revenue than Wall Street anticipated, while lifting its full-year adjusted earnings outlook. The cybersecurity company said after the closing bell Wednesday that it delivered record second-quarter net new annual recurring revenue and exceeded internal expectations across several metrics." —Wall Street Journal, August 27, 2025
My first reaction to the after-hours selloff was that the market completely missed the story. Fixating on a $10M Q3 revenue guide "miss" while ignoring record Net New ARR and the first concrete proof of Falcon Flex's consumption economics is classic short-term noise drowning out a transformative signal.
This wasn't a mixed quarter masquerading as success. This was the moment CrowdStrike demonstrated that its platform strategy isn't just theory—it's a self-reinforcing business model that's rewiring how enterprise cybersecurity gets consumed.
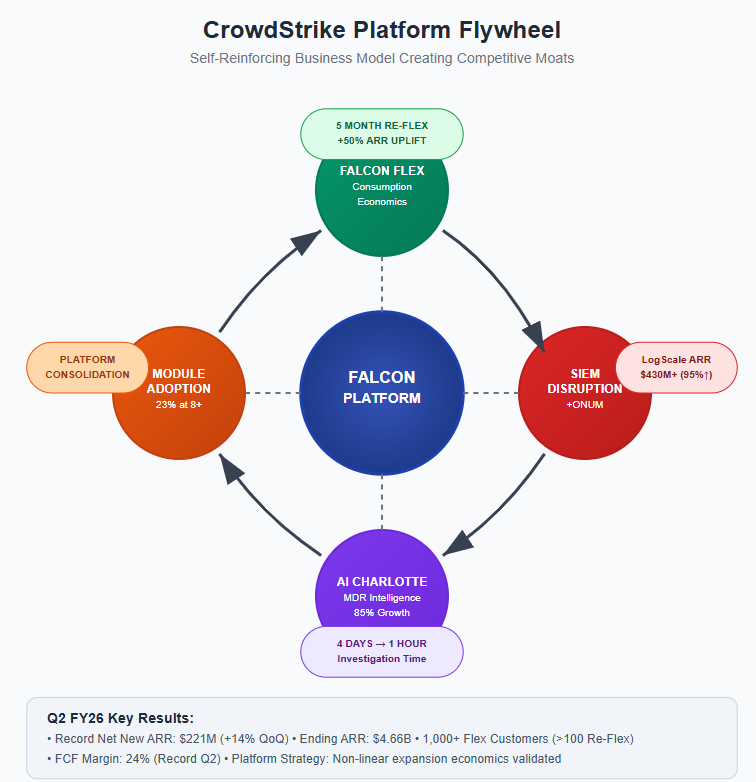
The Flex Flywheel Delivers Non-Linear Economics
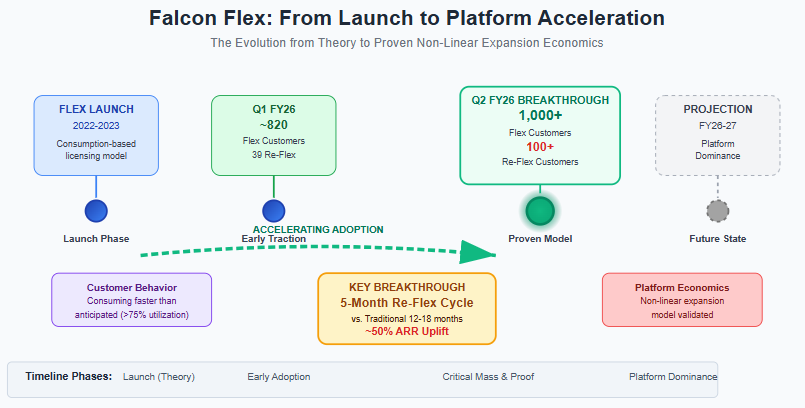
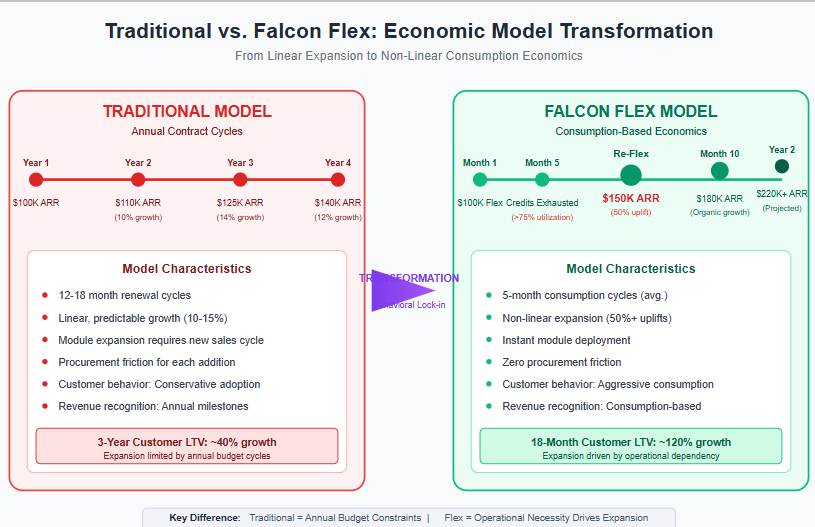
For two years, the CrowdStrike bull case has centered on Falcon Flex's theoretical potential to accelerate module adoption by removing procurement friction. The bear case dismissed it as fancy accounting to pull forward revenue. This quarter, we got the data that settles the debate.
The most telling metric: customers are exhausting multi-year credit commitments in five months and returning for 50% larger purchases. This isn't gradual platform adoption—it's consumption acceleration that transforms customer expansion from an annual sales process into a recurring inevitability.
CEO George Kurtz's language was deliberate: "Reflexes on average are yielding a nearly 50% uplift in Flex customer ending ARR, illustrating the strength of the Falcon platform and the power of our game changing licensing model."
He's not describing a pricing innovation—he's describing an economic engine that creates behavioral switching costs through operational dependency.
The flywheel mechanics are now clear: Flex removes procurement friction, customers consume faster than anticipated, operational workflows adapt to instant module deployment, switching back to traditional approval processes becomes painful, and re-Flex becomes inevitable at higher price points. This creates customer lifetime value expansion that compounds over time.
SIEM Displacement Strategy Removes the Last Friction Point
CrowdStrike's assault on legacy SIEM (Security Information and Event Management) vendors like Splunk has always been architecturally logical—why ship security data to external platforms when it's already generated and stored in Falcon? The challenge was data migration complexity. The ONUM acquisition eliminates that friction entirely.
Kurtz's explanation reveals the strategic sophistication: "Before, migrating data into next gen SIEM was a long pole in the displacement tent, often requiring third party tools. Our acquisition of ONEM is a direct response to a growing chorus of frustration." They identified the single biggest objection in SIEM sales cycles and bought the solution.
ONUM promises 5x event throughput, 50% storage cost reduction, and 70% faster incident response with real-time pipeline detection. But the deeper advantage is economic: CrowdStrike charges only for third-party data ingestion while legacy SIEM vendors tax all data processing. As customers deploy more Falcon modules, they generate more native telemetry that feeds the SIEM without additional costs.
This creates a structural cost advantage that compounds with platform adoption. Every new Falcon module makes CrowdStrike's SIEM relatively cheaper while making competitors' offerings relatively more expensive.
The AI Implementation Shows Platform Thinking
While every enterprise software company claims AI transformation, CrowdStrike's Charlotte implementation demonstrates the difference between platform integration and bolt-on features. The 85% quarter-over-quarter growth reflects immediate operational ROI that most AI initiatives lack.
Charlotte's competitive advantage isn't the underlying AI technology—it's the proprietary training dataset created by CrowdStrike's position as one of the world's largest MDR providers. As Kurtz explained: "Charlotte is constantly learning and improving as we train it on our market leading threat intelligence, battleground incident response, and scaled Falcon Complete MDR analyst behavior."
This creates a reinforcement learning loop where more customers generate better AI, which attracts more customers. Competitors can build AI security tools, but they can't replicate the "encyclopedia of threat telemetry" from managing 25,000+ customer security operations across every major breach incident.
The economic impact is measurable today: "Tasks that would take four days to actually investigate and understand are now taking an hour." This isn't future-state automation—it's present-day labor arbitrage that supports CFO Burt Podbere's guidance to 30%+ free cash flow margins in FY27.
Strategic Implications: Platform Network Effects at Enterprise Scale
The margin compression story—FCF margins declining despite 21% revenue growth—represents deliberate platform investment, not competitive weakness. Management's guidance for "at least 40% YoY net new ARR growth" in the back half represents unusually specific, falsifiable guidance that companies only make with exceptional pipeline visibility.
The quarter-early reacceleration validates that CrowdStrike successfully weaponized their post-incident period. Instead of just surviving the July 2024 outage, they accelerated customer platform consolidation through strategic concessions that are now generating compounding returns through the Flex flywheel.
What makes this particularly compelling is how the platform strategy creates self-reinforcing competitive advantages: more modules generate more data, which improves AI capabilities, which increases platform stickiness, which drives higher re-Flex rates, which accelerates module adoption. Each component strengthens the others.
CrowdStrike is successfully transitioning from a best-in-class product vendor to a strategic platform that's rewiring the economics of enterprise security operations. They're building a fortress business model protected by consumption behavioral lock-in and fueled by a proven flywheel that converts customer satisfaction into accelerated expansion.
The market's fixation on quarterly guidance optics while ignoring these fundamental platform dynamics represents exactly the kind of myopia that creates opportunities for investors focused on multi-year competitive positioning. This quarter wasn't a sign of weakness—it was definitive proof that the future of cybersecurity consolidation runs through CrowdStrike's platform, and they're just getting started.
Annexure
What is SIEM? (Security Information and Event Management)
At its core, a SIEM is a security control room for a company's entire digital world.
Imagine a massive building with thousands of doors, windows, and motion sensors. A security guard can't possibly watch every single camera feed at once. A SIEM is the central command center that collects the logs (the "event history") from all those sensors, analyzes them in one place, and alerts the security guards when something suspicious happens.
The Three Core Jobs of a SIEM:
Collect & Aggregate (The "I" for Information):
What it does: A SIEM's first job is to be a giant log collector. It pulls in event data from virtually every piece of technology in a company:
Endpoints: Laptops, servers, mobile phones (e.g., "User Bob logged into this laptop at 9:02 AM").
Network Gear: Firewalls, routers (e.g., "An unusual connection from an unknown country was just blocked").
Cloud Services: AWS, Azure, Google Cloud (e.g., "A new administrator account was just created in our cloud server").
Applications: Office 365, Salesforce (e.g., "Someone just downloaded 1,000 customer files").
Analogy: It’s like gathering all the security camera footage, door swipe records, and alarm system logs from every corner of the building and bringing them to one central video wall.
Correlate & Analyze (The "E" for Event):
What it does: This is the "smarts" of the system. A SIEM doesn't just show you the raw logs; it looks for suspicious patterns and connections across different systems. It correlates events to find a story.
Example: It might see these three separate, seemingly innocent events:
Bob logged in from a country he's never been to.
A few minutes later, Bob's account accessed the secret "Project X" server.
Then, a large amount of data was sent from that server to an unknown location.
Individually, these might not trigger a major alarm. But the SIEM connects the dots and says, "This isn't Bob. This looks like a coordinated attack!" and generates a high-priority alert.
Analogy: The security software doesn't just show the guards the raw footage. It automatically flags a sequence of events: "The person who swiped in with Bob's card at 3 AM just walked directly to the CEO's office and is now carrying a large, unidentified box out the back door."
Alert & Report (The "M" for Management):
What it does: When the SIEM finds a credible threat, it alerts the human security team (the Security Operations Center, or SOC) so they can investigate and respond. It also provides dashboards and reports for compliance and auditing (e.g., proving to regulators that they are monitoring their systems).
Analogy: This is the blaring alarm and the flashing red light on the security console, telling the guards exactly where to go and what to look for.
Why It's So Important (and Why CrowdStrike is Attacking It)
For Companies: A SIEM is often the "brain" of a company's security program. It's essential for detecting sophisticated attacks that might look like normal activity on any single device.
The Problem with Legacy SIEMs (like Splunk):
Expensive: They often charge based on the amount of data you send them (ingestion costs). As companies generate more data, the bills can become enormous.
Slow: Many were built for on-premise data centers, not the cloud. Searching through massive amounts of data can be slow, which is a critical problem when you're trying to stop an active attack.
Complex: They require a lot of human expertise to set up and manage.
CrowdStrike's Angle (Next-Gen SIEM): CrowdStrike's argument is that since their Falcon agent is already on the endpoints generating the most important security data (80-85% of it), it's incredibly inefficient to pay another company to ship and store that same data.
Their Pitch: "Just analyze the data where it already lives—on our platform. It will be faster, cheaper, and more effective because it's natively integrated."
In simple terms, a SIEM is the central detective for a company's digital life. CrowdStrike's strategy is to become not just the best security guard on every device, but also the smartest, most efficient detective in the central control room.
Disclaimer:
The content does not constitute any kind of investment or financial advice. Kindly reach out to your advisor for any investment-related advice. Please refer to the tab “Legal | Disclaimer” to read the complete disclaimer.