From Gate to Graph: The $28B Test of Cybersecurity's Control Plane
How Palo Alto Networks is betting that enforcement plus understanding beats architecture—and why the market may be mispricing both the opportunity and the risk
TLDR:
Security evolved from "gate to graph" - Traditional perimeter security dissolved with cloud/remote work, creating need for unified control planes that can govern distributed users, AI agents, and applications across any location
PANW's $28B assembly bet vs CrowdStrike's architecture - PANW is testing whether coordinating 4 separate platforms (SASE + Firewalls + XSIAM + CyberArk) can compete with CrowdStrike's single-agent platform that deploys 9 modules through one lightweight agent
Asymmetric risk at current prices - At $185 (50x P/E for 14% growth), market assumes near-perfect execution; probability-weighted upside is only 17% while assembly integration complexity creates meaningful downside risk - better to wait for entry points
The First Gatekeeper
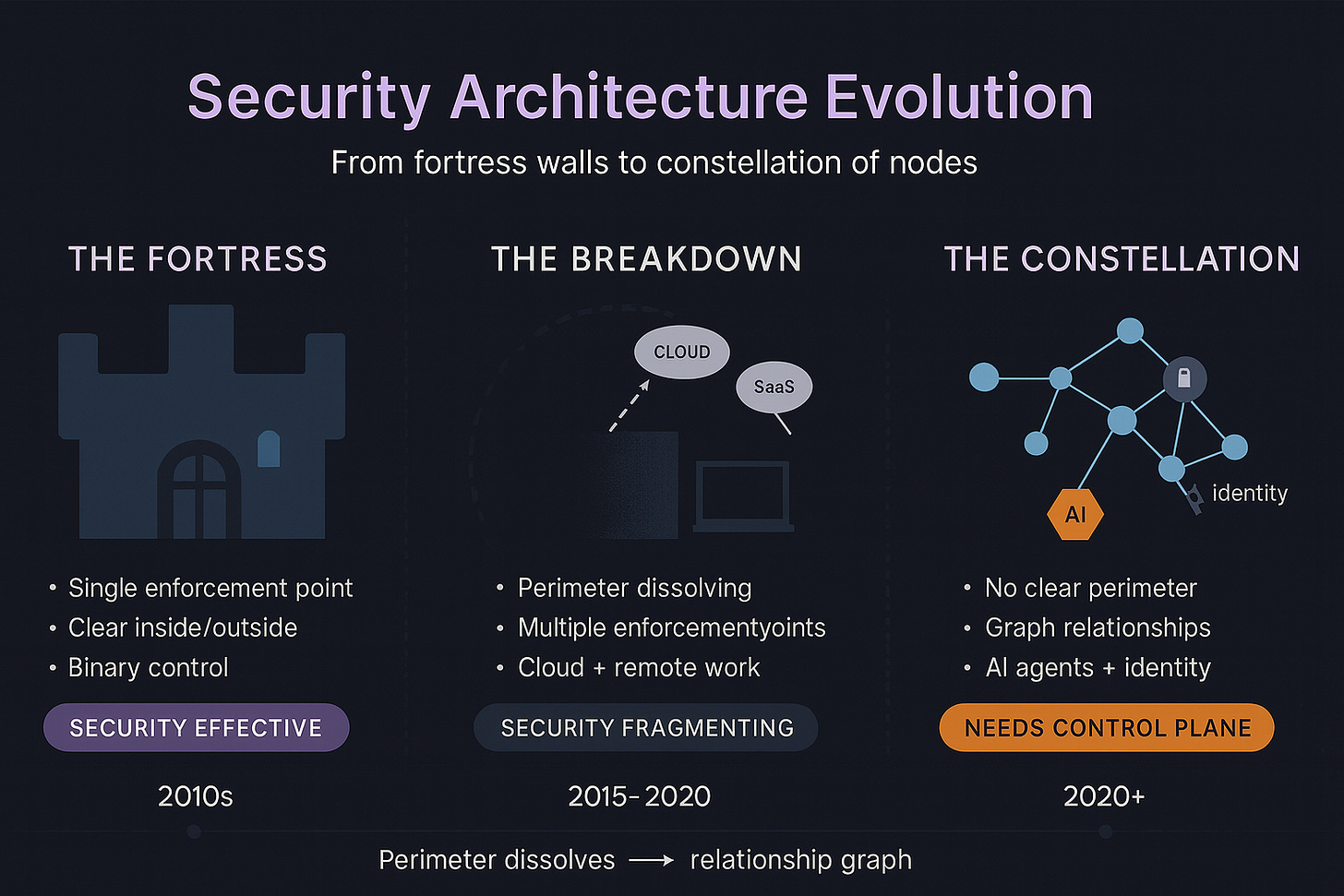
In the early 2010s, enterprise security had a beautifully simple model. The office was a fortress, employees worked within its walls, and next-generation firewalls stood guard at the perimeter. Palo Alto Networks built its first fortune by revolutionizing that gate—creating intelligent firewalls that could see "applications, not ports" and make nuanced decisions about what should pass through.
The security model was elegant in its clarity: strong perimeter, trusted inside, clear enforcement points. PANW's innovation was making the gatekeeper intelligent, capable of understanding not just the source and destination of network traffic, but the applications, users, and content flowing through their systems. They transformed network security from a simple allow/deny binary into sophisticated policy enforcement.
But then the world changed. Remote work exploded, SaaS applications proliferated, and cloud-first architectures dismantled the hub-and-spoke networks that made perimeter security possible. Users began living in browsers, data migrated to clouds, and AI agents started communicating directly with services across the internet. The perimeter didn't move to accommodate these changes—it dissolved entirely, transforming from a physical boundary into a graph of relationships between users, applications, data, and services.
This dissolution created a fundamental strategic question that reverberates through the cybersecurity industry today: If there's no single door to guard, where does security enforcement happen? The transition from "guarding the gate" to "governing the graph" represents more than technological evolution—it's a complete reimagining of how security works, where control should live, and who will capture the value from protecting increasingly distributed enterprises.
The World Turned Inside-Out
Today's enterprise exists as a constellation of relationships rather than a physical location. Users authenticate through browsers to access SaaS applications running across multiple cloud providers. AI agents autonomously access APIs, databases, and privileged systems to perform tasks that once required human intervention. Remote employees connect from home offices, coffee shops, and co-working spaces, accessing corporate resources through personal devices and public networks.
Security operations centers that once monitored well-defined network perimeters now struggle with a firehose of alerts from dozens of disconnected tools. Endpoint detection systems generate thousands of alerts. Cloud security platforms flag misconfigurations and suspicious behavior. Network monitoring tools report anomalies in traffic patterns. Email security gateways block phishing attempts. Each tool operates in isolation, creating fragmented visibility and requiring manual correlation to understand the broader threat landscape.
The old security model was fundamentally about blocking bad things at clearly defined boundaries. The new challenge is governing good things everywhere—ensuring that legitimate users, applications, and AI agents can access the resources they need while preventing unauthorized access, data exfiltration, and malicious behavior across a distributed architecture that has no clear inside or outside.
This transformation raises a critical strategic question that will determine the next decade of cybersecurity: Where should control and understanding live when no single enforcement point exists? Traditional approaches suggest distributing security across multiple specialized tools—endpoint agents for device security, network monitoring for traffic analysis, cloud controls for infrastructure protection. But a new generation of platform companies argues for a different approach: unified control planes that can enforce decisions and understand context across all surfaces simultaneously.
The winner of this architectural debate will likely capture the majority of enterprise security spending, as companies consolidate their fragmented tool collections into comprehensive platforms. Understanding which approach will prove superior—distributed specialization or unified control—may be the most important question facing cybersecurity investors today.
Palo Alto's Second Act: The Control Plane Strategy
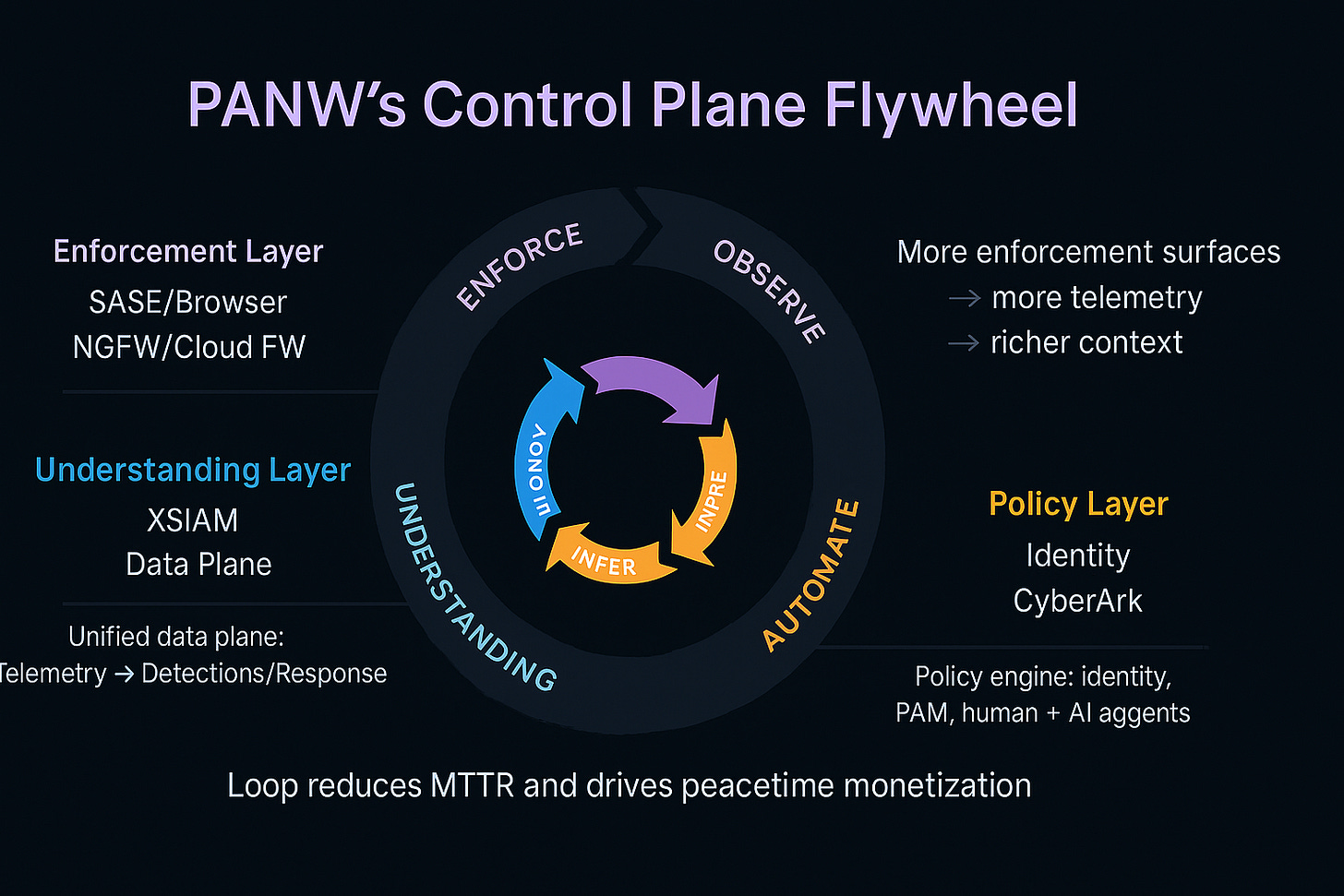
Palo Alto Networks is betting everything on a unified control plane approach, constructing what they call three surfaces of control that work together to govern the distributed enterprise.
The enforcement layer consists of inline security controls that can make real-time decisions about user and application behavior. Their Secure Access Service Edge (SASE) platform and Prisma Access Secure Browser create enforcement points for users accessing applications from any location. With over 6 million browser seats deployed and targeting 15 million, PANW is essentially embedding security enforcement into the user experience itself. Simultaneously, their virtual firewalls deployed in cloud environments create enforcement points for east-west traffic between applications and AI runtime communications.
The understanding layer centers on XSIAM, which PANW positions as the "operating system" for security operations centers. Rather than requiring security teams to manually correlate alerts from dozens of separate tools, XSIAM ingests telemetry from all enforcement points into a single data plane. This unified visibility enables what PANW calls "wartime" response—reducing mean time to resolution from hours to minutes when threats are detected. But perhaps more importantly, it enables "peacetime" monetization through modules like exposure management and email security that leverage the comprehensive data context.
The policy layer, soon to be enhanced by the $28B CyberArk acquisition, focuses on identity management as the governance engine for both human users and AI agents. As enterprises deploy autonomous AI agents with privileged access to corporate systems, traditional identity and access management becomes the critical control layer determining "who can do what, where" across the distributed enterprise.
What makes this strategy potentially powerful is the hidden flywheel connecting these three layers: Enforce → Observe → Infer → Automate → Enforce. More inline control surfaces generate more telemetry, which feeds into the unified data plane to create coherent context about threats and normal behavior. Better outcomes from faster response times drive adoption of additional modules and enforcement points. Standardization across platforms increases switching costs and creates more predictable cash flows.
The critical insight is that inline enforcement matters because security must govern before bad outcomes occur, not just detect after they happen. Traditional security approaches are fundamentally reactive—they identify threats and respond to incidents. PANW's control plane approach aims to be fundamentally preventive—making decisions about access and behavior in real-time before problems can occur.
This represents a fundamental shift in cybersecurity economics. Traditional approaches sell point solutions and hope for vendor consolidation over time. PANW's bet is on control plane economics—customers paying for comprehensive governance across multiple surfaces rather than individual security tools. You don't need traditional "seat-based" licensing to achieve seat-like lifetime value when browser/SASE deployment, peacetime security modules, and AI runtime governance create comprehensive per-user value.
The strategic inflection point driving this approach is the coming wave of AI agents in enterprise environments. Current identity and access management systems were designed for human users with predictable access patterns and approval workflows. AI agents will soon outnumber human users, operating autonomously with privileged access to sensitive systems and data. The company that can effectively govern AI agent permissions may control the next generation of enterprise security.
Competitive Landscape: The Control Plane Map
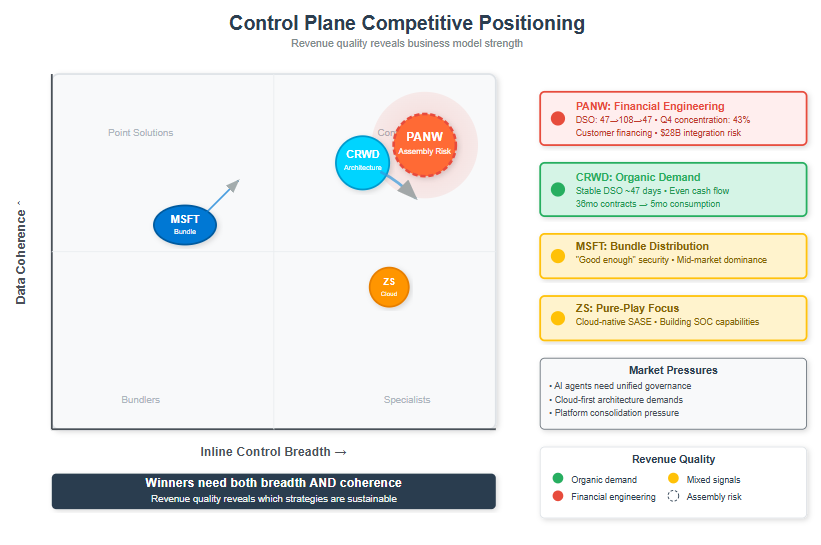
Understanding the competitive dynamics requires mapping players across two critical dimensions: inline control breadth (the ability to enforce decisions across multiple surfaces) and SOC/data coherence (unified understanding and decision-making capabilities). Winners in the platform era need both—enforcement without understanding is blind, while understanding without enforcement is powerless.
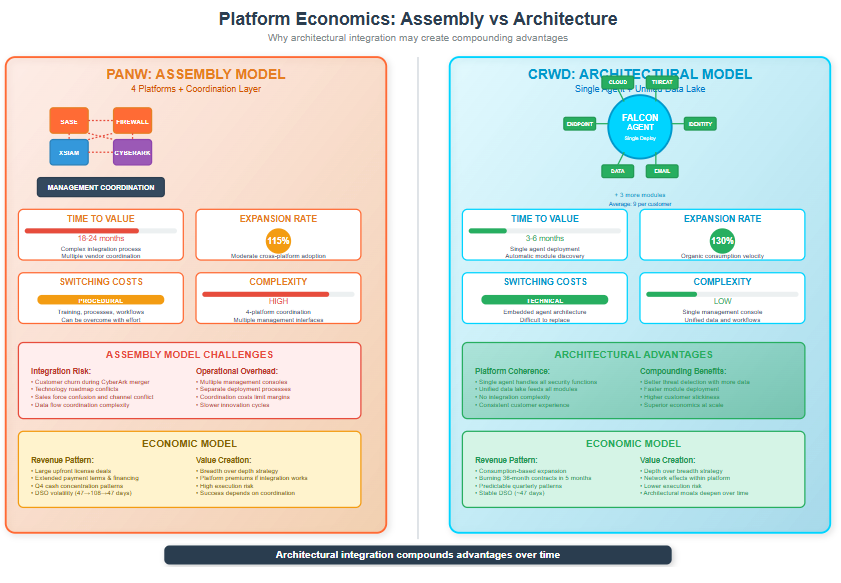
Palo Alto Networks positions itself in the upper-right quadrant, strongest when both inline enforcement and SOC unification are needed together. Their challenge is proving that sophisticated assembly integration—coordinating separate platforms through management processes—can compete with companies that built unified architectures from the ground up.
CrowdStrike occupies the upper-middle position with endpoint-centric SOC coherence and remarkable speed of module attachment. Their Falcon platform demonstrates true architectural integration—a single lightweight agent feeding a unified data lake that powers all security modules. The average CrowdStrike customer runs nine Falcon modules compared to the industry standard of four to five, and customers are "burning through" 36-month contracts in five months due to organic consumption acceleration. Their challenge is extending into inline control surfaces like browser and network security without breaking the agent coherence that makes their platform so effective.
Microsoft sits in the middle-left position, leveraging bundle strength to lift the security floor across their massive customer base. Their approach is fundamentally different—weaving "good enough" security throughout their productivity and cloud infrastructure rather than building specialized security tools. They struggle with mission-critical outcomes compared to specialists but have unmatched distribution advantages in the mid-market. Interestingly, Microsoft's bundling strategy doesn't threaten the specialists—it validates them by creating market bifurcation between commodity and mission-critical tiers.
Zscaler excels in the right-lower-middle position with cloud-native SSE/SASE capabilities but lighter SOC integration. Their purpose-built cloud security architecture offers advantages over hybrid approaches, but they're still building the data plane coherence needed for comprehensive security operations.
The competitive dynamics reveal different underlying demand patterns through revenue quality metrics. CrowdStrike shows infrastructure consumption psychology—customers organically expanding usage as they find more value in the platform. PANW shows sophisticated sales execution—with days sales outstanding oscillating between 47 and 108 days, Q4 cash concentration patterns, and aggressive customer financing programs to drive platform adoption.
What each player must prove reveals the fundamental strategic questions facing the industry. PANW must demonstrate that browser seat scale, XSIAM peacetime economics, and AI runtime governance can create genuine control-plane lifetime value. CrowdStrike must maintain their Flex consumption velocity while extending into inline control without compromising their single-agent coherence. Microsoft must translate suite breadth into reliable outcomes at enterprise scale while specialists must defend their mission-critical positioning against bundling pressure.
The architecture question underlying all competitive dynamics is whether sophisticated coordination can compete with single-platform purity or ecosystem integration. CrowdStrike's technical switching costs—embedded agents that become integral to security operations—appear more durable than PANW's procedural switching costs based on training and process familiarity. But PANW's broader enforcement surface may create different value propositions that aren't directly comparable.
The CyberArk Move: $28B Architectural Test
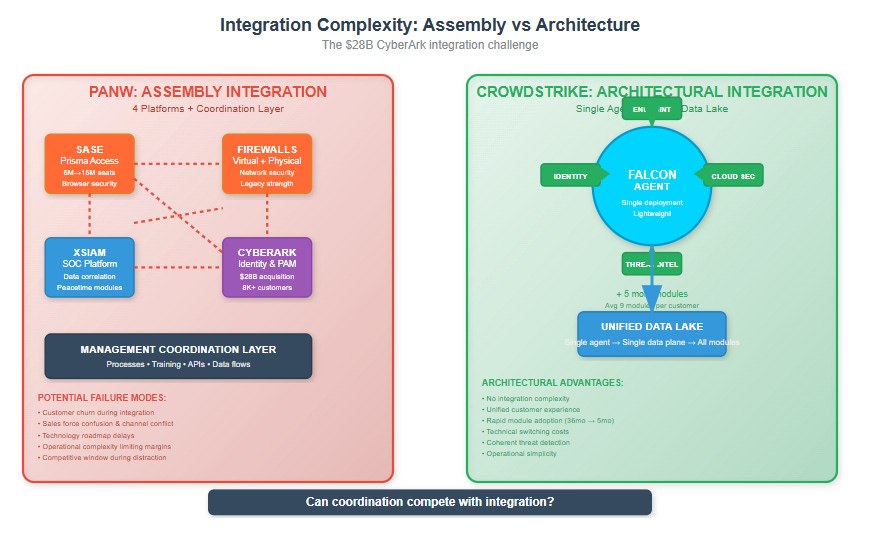
PANW's announced acquisition of CyberArk for $28B represents the ultimate test of their assembly integration approach. The strategic objective is clear: make identity management the policy engine that governs both human users and AI agents across browser, network, and cloud enforcement surfaces.
Rather than building identity capabilities internally, PANW chose to acquire the incumbent leader with 8,000+ enterprise customers and deep expertise in privileged access management. This approach promises faster enterprise trust and policy unification, creating what PANW envisions as a unified policy loop: identity signals feeding into XSIAM decisions that drive inline enforcement across browser, SASE, and cloud platforms.
The integration challenge is enormous. PANW must unify privileged access management with SASE, firewalls, and XSIAM—essentially coordinating four major platforms through management processes while maintaining customer satisfaction and competitive differentiation. The go-to-market complexity involves training PANW's sales force on identity solutions while potentially maintaining CyberArk's specialized motion, managing channel conflicts, and avoiding confusion in the field.
From a customer perspective, the integration must seamlessly combine 8,000+ CyberArk customers with 75,000+ PANW customers through a major technology and operational transformation. The financial targets are aggressive: 40%+ free cash flow margins by FY2028, which requires operational leverage that assembly models often struggle to achieve due to coordination complexity.
Compare this to CrowdStrike's organic expansion into identity and cloud security, where new capabilities plug directly into their existing single-agent architecture. CrowdStrike customers get identity protection through the same Falcon agent they're already running, with unified data flowing into the same threat graph. There's no separate sales motion, no additional deployment complexity, and no integration risk.
The key integration metrics that will validate or invalidate PANW's approach include: the percentage of large enterprise license agreements that include PAM, SASE, and XSIAM together; identity telemetry driving XSIAM threat detections; and time-to-policy deployment for AI agents. Success requires not just technical integration but organizational alignment, customer adoption, and competitive differentiation.
The risk factors are substantial: integration complexity could create customer churn and operational inefficiencies; roadmap execution could slow while teams focus on coordination rather than innovation; competitive responses during the distraction period could capture market share; and the fundamental question of whether sophisticated management can deliver equivalent economics to architectural integration remains unanswered.
This acquisition represents more than market expansion—it's a $28B test of whether assembly integration can scale to compete with architectural integration in winner-take-most markets. The outcome will likely determine not just PANW's future but the viability of assembly approaches across the technology industry.
Investment Case: Control Plane Economics vs. Assembly Risk
The investment challenge is that the market currently treats PANW as a successful platform transformation story deserving premium multiples, but may be missing both the control-plane economics potential and the assembly integration risks that make this situation more complex than traditional platform analysis suggests.
Market belief: PANW is successfully executing a platform transformation that justifies premium valuation through consolidation leadership; architectural approaches between competitors are functionally equivalent.
Our view: The market is missing the potential for genuine control-plane economics from browser deployment, peacetime XSIAM modules, identity governance, and AI runtime management, while simultaneously underpricing the assembly integration risk and revenue quality concerns that suggest different underlying competitive dynamics than pure platform plays.
The catalyst: CyberArk integration success or failure will validate or invalidate the assembly approach versus architectural integration, likely creating significant valuation adjustments in either direction.
Detailed Scenario Analysis
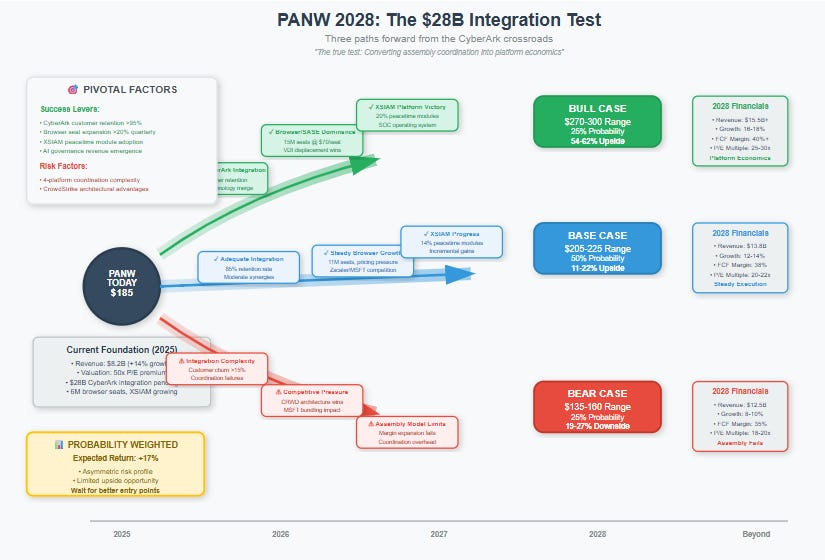
Bull Case: $270-300 (25% probability) - "Control Plane Dominance"
The bull case assumes PANW successfully executes the most ambitious version of their control plane strategy. Browser/SASE deployment would expand to 15+ million seats at $60-80 per seat, compared to current deployment of approximately 6 million seats at roughly $50 per seat. This expansion would be driven by virtual desktop infrastructure displacement and comprehensive remote access governance.
XSIAM would reach $3.5B+ in annual recurring revenue with 20%+ coming from peacetime modules like exposure management and email security that monetize the comprehensive data context. This assumes successful positioning of XSIAM as the central nervous system for security operations rather than just another SIEM replacement.
Identity integration would achieve 30%+ cross-sell into the existing PANW customer base while maintaining 95%+ CyberArk customer retention through the integration process. AI governance would become a major revenue driver as enterprises deploy 10+ million AI agents under management, requiring sophisticated permission and access controls.
Overall revenue would grow at 16-18% CAGR through FY2027, reaching $15.5B. Operating margins would expand to 38-40% as infrastructure economics emerge and AI automation reduces manual security operations. Free cash flow margins would sustain 40%+ as control plane standardization reduces customer acquisition costs and creates more predictable revenue streams.
Competitively, PANW would win 60%+ of large platform consolidation deals versus CrowdStrike as customers prioritize comprehensive enforcement over single-agent purity. Microsoft's bundling would plateau at the mid-market while enterprises choose mission-critical specialists for core security operations.
The valuation framework would shift toward infrastructure utility multiples (25-30x P/E) rather than growth software as cash flow predictability improves and platform characteristics become apparent. The mathematical outcome: $15.5B revenue × 40% FCF margin × 23x multiple ÷ 680M shares = $285/share.
Base Case: $205-225 (50% probability) - "Steady Execution"
The base case assumes solid execution without breakthrough platform transformation. Browser/SASE would reach 10-12 million seats but face pricing pressure from Zscaler and Microsoft competition. XSIAM would show steady growth but remain primarily focused on core security operations rather than transformational peacetime monetization, with 12-15% of revenue from additional modules.
CyberArk integration would proceed adequately with 15-20% cross-sell into the PANW base and moderate customer churn during the transition period. Overall revenue would grow at 12-14% CAGR, reaching $13.8B—essentially tracking industry growth rates without major market share gains.
Operating margins would plateau at 32-35% as coordination costs limit operational leverage opportunities. Free cash flow margins would remain stable at 38-39% without breakthrough automation or efficiency gains. Market share would remain roughly stable versus competitors as the platform story works but doesn't create major differentiation.
Valuation multiples would compress toward mature software levels (20-22x P/E, 28-30x FCF) as growth moderates and platform transformation proves incremental rather than transformational. The mathematical outcome: $13.8B revenue × 38% FCF margin × 28x multiple ÷ 680M shares = $216/share.
Bear Case: $135-160 (25% probability) - "Assembly Complexity"
The bear case assumes that assembly integration challenges become apparent under competitive pressure. Browser/SASE growth would be limited by Microsoft Teams integration and Zscaler competition, while XSIAM adoption would be slower than expected with peacetime modules generating less than 10% of revenue.
CyberArk integration would face execution challenges with 15%+ customer churn and limited synergy realization as coordination complexity exceeds management capabilities. Overall revenue would grow at 8-10% CAGR, reaching $12.5B as PANW maintains market presence but loses share to architectural integration competitors.
Operating margins would decline to 28-30% due to integration costs and competitive pricing pressure. Free cash flow margins would compress to 35-36% as higher customer acquisition costs and coordination inefficiencies offset scale benefits. CrowdStrike's architectural advantages would become apparent in head-to-head competition as customers prioritize platform coherence over breadth.
Valuation would reflect quality software with risk discount (18-20x P/E, 25-27x FCF) as integration concerns and competitive pressure create uncertainty about long-term positioning. The mathematical outcome: $12.5B revenue × 35% FCF margin × 26x multiple ÷ 680M shares = $149/share.
Valuation Reality Check
The probability-weighted expected value of approximately $215/share suggests 16% upside from current levels around $185, but this analysis reveals asymmetric risk rather than asymmetric opportunity. The limited upside potential combined with meaningful downside risk creates an unfavorable risk/reward profile for investors buying at current valuations.
Current multiples of 50x P/E for 14% growth are extreme by any software standard, though PANW's 38% free cash flow margins provide meaningful downside protection. High-quality software companies rarely trade below 6-8x EV/Sales regardless of execution challenges, suggesting a valuation floor around $140-160 based on software company benchmarks.
At $185, PANW presents asymmetric risk that favors waiting for better entry points rather than paying platform premiums for uncertain transformation outcomes.
What to Watch: Signposts and Metrics
The investment thesis will be validated or invalidated by specific operational and financial metrics that reveal whether control plane economics are emerging or assembly integration is hitting complexity limits.
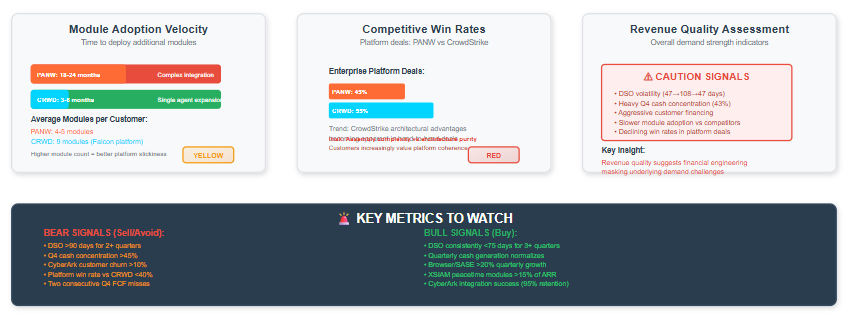
Bull Case Validation Signals include revenue quality normalization with DSO consistently below 75 days for three or more quarters, indicating organic demand strength rather than financial engineering. Browser/SASE scale metrics should show net new seats growing above 20% quarterly with average revenue per seat expanding and evidence of VDI displacement wins. XSIAM economics should demonstrate peacetime modules reaching 15-20% of XSIAM ARR with ARR per customer expanding above 25% annually.
Integration execution success would be evidenced by CyberArk customer retention above 95% and identity telemetry driving over 30% of XSIAM detections. AI governance traction should show 1+ million AI agents under management with AI Access attach rates above 60% to browser deployments.
Bear Case Warning Signals include revenue quality deterioration with DSO exceeding 90 days for two or more quarters, suggesting intensifying financial engineering to maintain growth targets. Competitive pressure would be apparent through win rates versus CrowdStrike falling below 50% in platform deals and increasing pricing discounts to maintain market share.
Integration challenges would manifest through CyberArk customer churn above 10%, roadmap delays, and sales force confusion in the field. Growth deceleration below 12% revenue growth, stalling browser seat expansion, and slower than expected XSIAM adoption would indicate competitive pressure and market saturation.
The Ultimate Test: Cash Flow Consistency
The most revealing metric may be quarterly cash flow patterns, particularly Q4 collections relative to scheduled deferrals. Infrastructure businesses typically demonstrate predictable quarterly cash generation, while assembly models requiring complex coordination often show volatile collection patterns as they manage sophisticated customer relationships and financing arrangements.
Consistent, predictable cash generation would support the infrastructure transformation narrative and suggest genuine platform economics. Continued quarterly volatility in collections would suggest ongoing financial engineering rather than platform economic strength. Two consecutive Q4 free cash flow misses would fundamentally change the valuation framework as investors lose confidence in execution predictability.
Risk Assessment: Ranked by Impact × Probability
CyberArk Integration Execution (High Impact × Medium Probability) represents the highest priority risk factor. The $28B bet on assembly model scaling could validate architectural integration advantages if customer churn, technical complexity, or sales disruption prove unmanageable. Success would validate sophisticated coordination approaches; failure would demonstrate the limits of assembly integration.
Revenue Quality Deterioration (Medium Impact × High Probability) reflects DSO patterns suggesting aggressive customer acquisition tactics. Normalization could reveal underlying demand weakness that's currently masked by financing programs and trade-in incentives.
Competitive Architecture Advantages (High Impact × Medium Probability) could emerge as CrowdStrike's single-agent platform proves superior under competitive pressure while Microsoft's bundling commoditizes the mid-market, leaving PANW caught between architectural purity and ecosystem integration.
Collections Concentration (Medium Impact × Medium Probability) creates quarterly volatility through Q4 cash dependency. Two consecutive misses would change investor perception about business model predictability and platform characteristics.
AI Governance Timing (Medium Impact × Low Probability) represents potential upside if agentic AI adoption accelerates faster than expected, but also risk if adoption proves slower than PANW's investment thesis assumes.
Operational Leverage Ceiling (Medium Impact × Medium Probability) could emerge if assembly coordination hits complexity limits that prevent the margin expansion required to justify current valuations and financial targets.
From Gate to Graph
The fundamental transformation from guarding physical perimeters to governing relationship graphs represents more than technological evolution—it's a complete reimagining of where control and understanding should live in distributed enterprises. The winner will be whoever can most effectively enforce decisions and understand context across the entire graph of users, applications, data, and AI agents.
PANW's bet on sophisticated coordination creating control plane economics competitive with architectural integration represents one of the most significant strategic experiments in enterprise technology. The CyberArk acquisition is the ultimate validation test—$28B invested in proving that assembly integration can scale to compete with purpose-built platforms in winner-take-most markets.
Success would demonstrate that sophisticated management can overcome coordination complexity to deliver platform economics through comprehensive enforcement and understanding. Failure would suggest that architectural advantages compound over time and cannot be overcome through financial engineering or operational coordination.
For investors, this creates an unusual opportunity to observe a natural experiment in platform construction with billions of dollars in market value at stake. The patient capital advantage belongs to those who can distinguish between genuine platform transformation and sophisticated suite coordination—and wait for integration challenges or competitive pressure to create attractive entry points.
PANW may indeed be building genuine control plane value that justifies premium valuations, but current pricing assumes perfect execution of an untested assembly integration approach. The risk/reward profile favors waiting for clarity on whether enforcement plus understanding can compete with architectural purity, rather than paying platform premiums for coordination experiments.
The evolution from gate to graph is irreversible, but the winner of the control plane competition remains undetermined. The next 18 months will reveal whether sophisticated assembly can govern the distributed enterprise as effectively as architectural integration—and whether investors paying today's premiums will be rewarded for their confidence or reminded that in technology markets, architecture eventually beats marketing.
General Disclaimer
The information presented in this communication reflects the views of the author and does not necessarily represent the views of any other individual or organization. It is provided for informational purposes only and should not be construed as investment advice, a recommendation, an offer to sell, or a solicitation to buy any securities or financial products.
While the information is believed to be obtained from reliable sources, its accuracy, completeness, or timeliness cannot be guaranteed. No representation or warranty, express or implied, is made regarding the fairness or reliability of the information presented. Any opinions or estimates are subject to change without notice.
Past performance is not a reliable indicator of future performance. All investments carry risk, including the potential loss of principal. This communication does not consider the specific investment objectives, financial situation, or particular needs of any individual.
The author and any associated parties disclaim any liability for any direct or consequential loss arising from the use of this material and undertake no obligation to update or revise it.



The quality of the analysis is excellent - well done ! Where can I access the previous analyses over the lastctwo months since launch ? Please share / let me know thank you